Dynamic Application Security Testing (DAST)
Learn how DAST actively investigates running applications with penetration tests to detect possible security vulnerabilities.
Explore InsightAppSecTopic Overview
- What is Dynamic Application Security Testing (DAST)?
- Why Do You Need a DAST Tool?
- How DAST Tools Enhance Web Application Security
- Three Tips for Dynamic Application Security Testing
What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is a procedure that actively investigates running applications with penetration tests to detect possible security vulnerabilities.
Web applications power many mission-critical business processes today, from public-facing e-commerce stores to internal financial systems. While these web applications can enable dynamic business growth, they also often harbor potential weaknesses that, if left unidentified and unremediated, could quickly lead to a damaging and costly data breach.
To address this growing threat, businesses are increasingly deploying dynamic application security testing (DAST) tools as part of a more security-forward approach to web application development. DAST tools provide insight into how your web applications behave while they are in production, enabling your business to address potential vulnerabilities before a hacker uses them to stage an attack.
As your web applications evolve, DAST solutions continue to scan them so that your business can promptly identify and remediate emerging issues before they develop into serious risks.
Why Do You Need a DAST Tool?
Web application attacks may not get the same headlines that ransomware exploits do, but they are without question a major threat to businesses of all kinds. One of the most common web-based attacks is SQL injection (SQLi), in which an adversary can gain complete control over a company’s web application database by inserting arbitrary SQL code into a database query.
Another is cross-site scripting (XSS), in which attackers inject their own code into a web application with which they may then steal user credentials, session cookies, or other sensitive information—with neither the user nor the company having any idea that this has happened.
Hackers are known to target content management systems and e-commerce platforms in particular because they can harbor a concentration of vulnerabilities that, once discovered, can easily be exploited over and over. Once a web application attack is in progress, the security team may not detect it for quite some time.
Meanwhile, the attacker has free rein to wreak as much havoc as possible, helping themselves to sensitive corporate and even client data that may lie in the database behind the web application, such as credit card numbers or personally identifiable information (PII).
Unfortunately for businesses, even relatively unskilled hackers can easily launch these kinds of attacks and, with the prospect of lucrative paydays, they are especially motivated to do so. They typically look for easily exploitable vulnerabilities in a web application, such as those found in the OWASP Top 10, with which they can stage a cyber-assault.
DAST tools operate in a similar way, giving your security and development teams timely visibility into application behaviors and potential weaknesses that could be exploited before an enterprising hacker discovers and capitalizes on them.
How DAST Tools Enhance Web Application Security
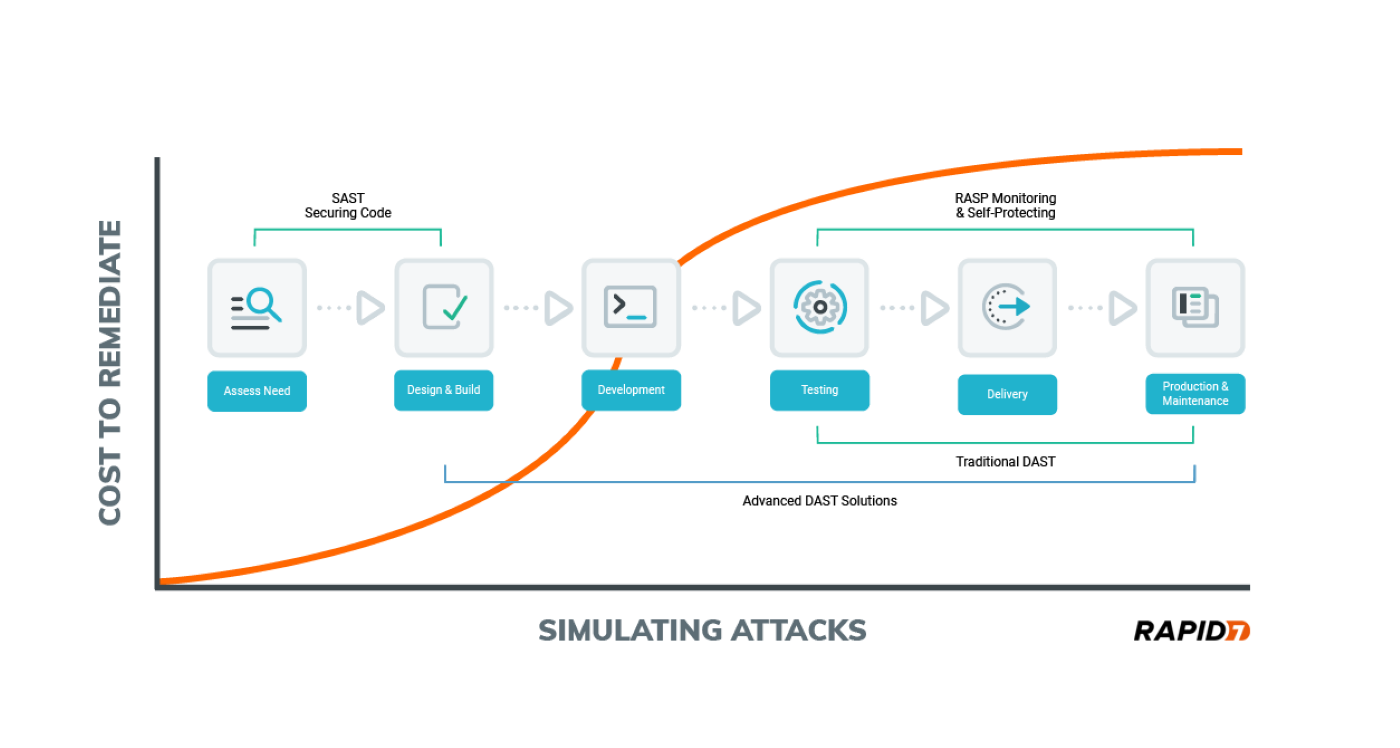
DAST tools continually search for vulnerabilities in a web application that is in production, hunting for weaknesses that attackers could try to exploit and then illustrating how they could remotely break into the system. Upon identifying a vulnerability, a DAST solution sends automated alerts to the appropriate teams so they can prioritize and remediate it.
With DAST tools, businesses can better understand how their web applications behave, continually highlighting new and emerging weaknesses as they evolve. By using DAST to identify vulnerabilities earlier in the software development lifecycle (SDLC), companies can reduce risk while saving time and money.
Businesses can also use DAST to assist with PCI compliance and other types of regulatory reporting. Some companies may voluntarily use the OWASP Top 10 list of risks to application security as a compliance benchmark. Alternatively, third parties may request that the companies evaluate their own web applications and remediate the top vulnerabilities on that list.
In addition to streamlining compliance, a DAST solution can also help developers spot configuration mistakes or errors and highlight specific user experience problems with web applications.
Three Tips for Dynamic Application Security Testing
1. Use DAST early and often for best results
Companies reap maximum benefit from a DAST solution when they leverage it to identify potential weaknesses in their web applications, particularly mission-critical applications, as early as possible in the software design lifecycle. Companies that do not deploy DAST early on in the SDLC may find that it unnecessarily costs them far more money and staff time—not to mention a significant amount of frustration—to remediate the issues that they find.
2. Enable effective collaboration with DevOps
DAST tools help you prioritize the vulnerabilities you discover, but to ensure proper resolution, you must then effectively hand them off to your colleagues in the DevOps team. For this reason, it’s a good idea to fully integrate your DAST tools with the bug-tracking system your DevOps colleagues use. By providing your developers with precisely the right information they need to promptly remediate vulnerabilities, you can help them make security concerns a priority and bring your company closer to a DevSecOps mindset.
3. DAST works best as part of a comprehensive approach to web application security testing
Although DAST can give busy security teams timely insight into the behavior of web applications once they are in production, SAST and application penetration testing are other effective forms of web application security testing that businesses often deploy in combination with DAST. SAST creates a useful snapshot of vulnerabilities in an application’s source code, which is especially valuable early on in the SDLC. Application penetration testing provides a real-world demonstration of exactly how an attacker might break into a specific web application.
With web application attacks on the rise, businesses are increasingly realizing that they must prioritize web application security early in the SDLC. By implementing a web application security scanner and incorporating some basic best practices for both web application security testing and vulnerability remediation, they can significantly reduce their risk and help keep their systems safe from opportunistic attackers.
Read More About DAST
Learn about Rapid7's DAST Product
DAST: Latest News from the Blog